Organizations
All tests run by XTC are organised in test projects, which in turn are part of an organization.
Organizations can only be created by an XTC admin. They will also assign an initial administrator for every organization, who will have permissions to add additional members to the organization, and, most importantly, create projects in the organization’s context.
Organization Configuration
In Configuration, you may edit the name, short name and description of your organization as well as upload an organization logo (which will also be displayed when the organization is shown in the list on the Dashboard page).
In the Security tab, you may enable or disable user invitations or define authorization requirements for the members of your organization.
The Integrations tab allows you to integrate XTC with your Slack Workspace to be notified of certain events like load test status changes. See the Slack Integration for further details.
User Roles Within an Organization
As an organization member, a user account can have one of the following roles:
- as a guest, you can only view the organization’s dashboard,
- a member is basically the default role for any new project user and is allowed to view organization settings and view and work on projects,
- a billing manager has permission to view and evaluate resource usage of the organization, and
- as an organization administrator you have complete permissions to change the organization’s projects, members and configuration.
(Permissions increase in order of the list, i.e. a billing manager has the same permissions as a member plus some in addition to that.)
If you are logged in and are currently viewing an organization, your role will be displayed at the bottom right in the footer:
Adding Members to an Organization
To add new members to the organization, select Members in the menu on the left. You will see the list of members, including their Login Provider/2FA settings and the time of their last login.
By clicking the + sign in the top right, you can add new members by typing the name (mail address) of their user account and assigning one of the roles from above. The user you want to add needs to be signed up with this e-mail address already.
If you want to add multiple users at once, simply paste a list of e-mail addresses (separated by comma, newline or space). All users will be assigned the same role.
The Members page of an organization shows the login provider for every member and whether or not a member has 2FA enabled. This way, organization admins can easily check if certain security requirements imposed by the organization are met.
Explicitly assigning organization members is usually not necessary in your daily work, as organization membership and roles are assigned implicitly by adding and removing project members.
Inviting Users to Join XTC
As an org admin you may invite users who do not have an XTC account yet to join your org in XTC (if this feature is enabled). Simply add these users to your organization as usual, but make sure you activate the Invite Users toggle.
Users invited this way will receive an email with a link to complete their registration (provide name, password, etc.). Once this is done, these users are all set and ready to participate in the organization.
Invitations are valid for 30 days. Organization administrators may resend the invitation for an invited user from the Members page at any time. Users who have once been invited to join an organization, but have not completed the registration process, will be automatically deleted after 90 days.
Editing and Removing Org Members
To update a user’s role within an organization, go to the Members page and click the context menu right of the user name, then select Edit Role. You can then pick a new membership role.
To remove members from an organization, go to the Members page and click the context menu right of the user name, then select Remove (you will be prompted to confirm the deletion).
Locking Members of an Organization
When a user is a member of an organization, but does not yet or no longer fulfill the current requirements imposed by the organization (mostly security-related), the user should be locked out, either automatically by the system or manually by an admin of the organization. When locked, the user remains a member of this organization, but can no longer see any data or perform any action.
To lock out a user manually, open the Members page, locate the user in question and click Lock Member in the context menu. To unlock the user again, click Unlock Member.
Mandatory Login Requirements
Organization admins may impose mandatory login requirements on users of their organization. They may require users to be authenticated using specific login providers or 2FA.
The configuration does not force users to actually configure the required login procedure to be able to log into XTC. It merely prevents them from accessing the organization. Users will still be able to see the organization in their dashboard and organization dropdown, but will see an appropriate error screen informing them about the need to comply with the login requirement when trying to access the organization details. Organization admins should inform users via appropriate means to ensure that they are up-to-date on any login changes.
When accessing an organization, the system will check whether the login requirements are fulfilled in the current session. Users that have an external login provider and 2FA configured will need to use the appropriate login flow to access a specific organization. This can mean having to log out and log in again using a different authentication method in order to switch organizations.
Changes to the login requirement take effect immediately. Users that are already logged in will get the appropriate lock-out message on their next access to any of the organization’s data. This includes saving any changes they may have made in the meantime. Admins should therefore try to schedule changes in a way to minimize user impact (e.g. outside of business hours or during an announced maintenance window).
XTC currently does not support requiring both, 2FA and SSO login. If your security policies require this setup please configure your SSO provider as the sole allowed login method and configure 2FA as a requirement in your provider’s setup.
Mandatory Two-Factor Authentication
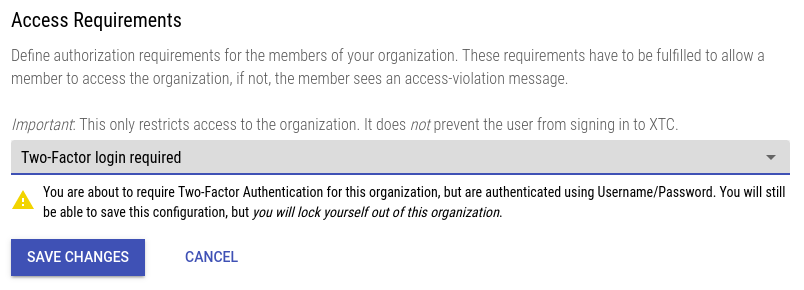
To enable mandatory 2FA for an organization go to the organization’s Configuration, open the Security tab and edit Access Requirements. Select the value Two-Factor login required and save the changes.
Accidental Lockout
If you are not currently logged in via 2FA the system will warn you about locking yourself out of the organization (see example screenshot). Take this warning seriously as you will not be able to access the organization (and therefore change the login requirement) after saving the configuration!
Mandatory Login via an External Provider
To enable the mandatory use of an external login provider go to the organization’s Configuration, open the Security tab and edit Access Requirements. Select the value SSO login required and save the changes.
Admins can allow a specific set of login providers by putting their issuer URLs into the text field. Issuer URLs are the exact values of the iss claim in the OpenID Connect access token signed by your provider (e.g. https://accounts.google.com for the public Google identity provider). The system supports multiple allowed issuers by putting each URL on a seperate line.
Accidental Lockout
If you are not currently logged in via an external provider the system will warn you about locking yourself out of the organization. Take this warning seriously as you will not be able to access the organization (and therefore change the login requirement) after saving the configuration!
Admins should be logged in via the login provider they intend their users to use, if possible. The system checks your current issuer against the entries in the list while entering them and therefore provides immediate feedback regarding any typos in the URL.